Cyber Security Money Making Threats
Driven by Money
There are a few key threats organizations face frequently:
- Ransomware files and systems are encrypted with attackers keys and they demand you to pay money to get your data back.
- Cryptocurrency miners; your systems are infected with a low-profile cryptocurrency mining tool. This tool uses the CPU to try make money on a cryptocurrency for the attackers.
- BEC ("Business Email Compromise"). Users get hacked through all sorts of methods and their emails are compromised. Via email compromise the attackers can intercept communications, for example an invoice, and try to redirect payments to other banks and accounts.
There are plenty of ways of making money for cyber criminals, which attracts people and interest.
Value and Power
There is value and power in many things related to IT, for example:
- Bandwidth can be used to pressure businesses by targeting them with DDOS ("Distributed Denial of Service") attacks.
- Hacked systems may have sensitive information worth money, for example business proprietary information, online gaming assets, sensitive photographs and pictures.
- Attackers can install themselves in browsers and try to hijack the online banking use.
The potential for criminals to make significant amounts of money within the cyber domain causes more and more criminal gangs and other opportunists to join in on the action and make our lives much harder.
Threatening for Money
Another common attack cyber criminals perform to make money is the act of extortion, that is holding individuals hostage based on information they have on a individual, trying to make them pay money to be released from the extortion attempt. Consider the following common scenario:
- A person meets up with someone online, the other party is actually a scam artists trying to trick the victim.
- They engage in interesting conversations and seem to make an immediate deep bond between one another.
- They might even engage in video conversations, but the scam artists is for example using recorded video or simply has an excuse for not being able to activate their microphone or web-camera.
- One thing might lead to another and the relationship could turn sexual. The scam artist tries to convince the victim in giving up personal pictures and recordings of themselves, likely in compromising situations.
- Once the scam artist receives this material, perhaps even returning fake pictures of innocent people in similar situations, the extortion begins.
- The scam artist can now threaten to release the compromising material to family members, co-workers and others, offering to delete the material if a sum of money is paid into the scam artists account.
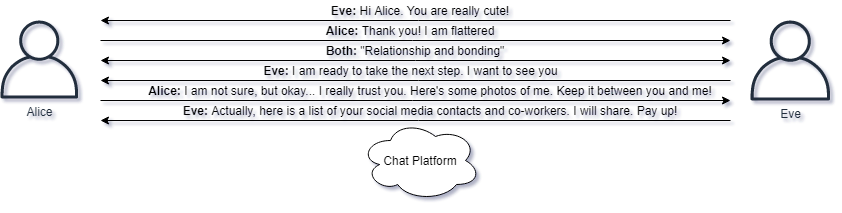
Stories like these are far from uncommon, and there exists countless of different scenarios and opportunities for criminals to benefit from victims using the Internet without knowing the risks associated.


